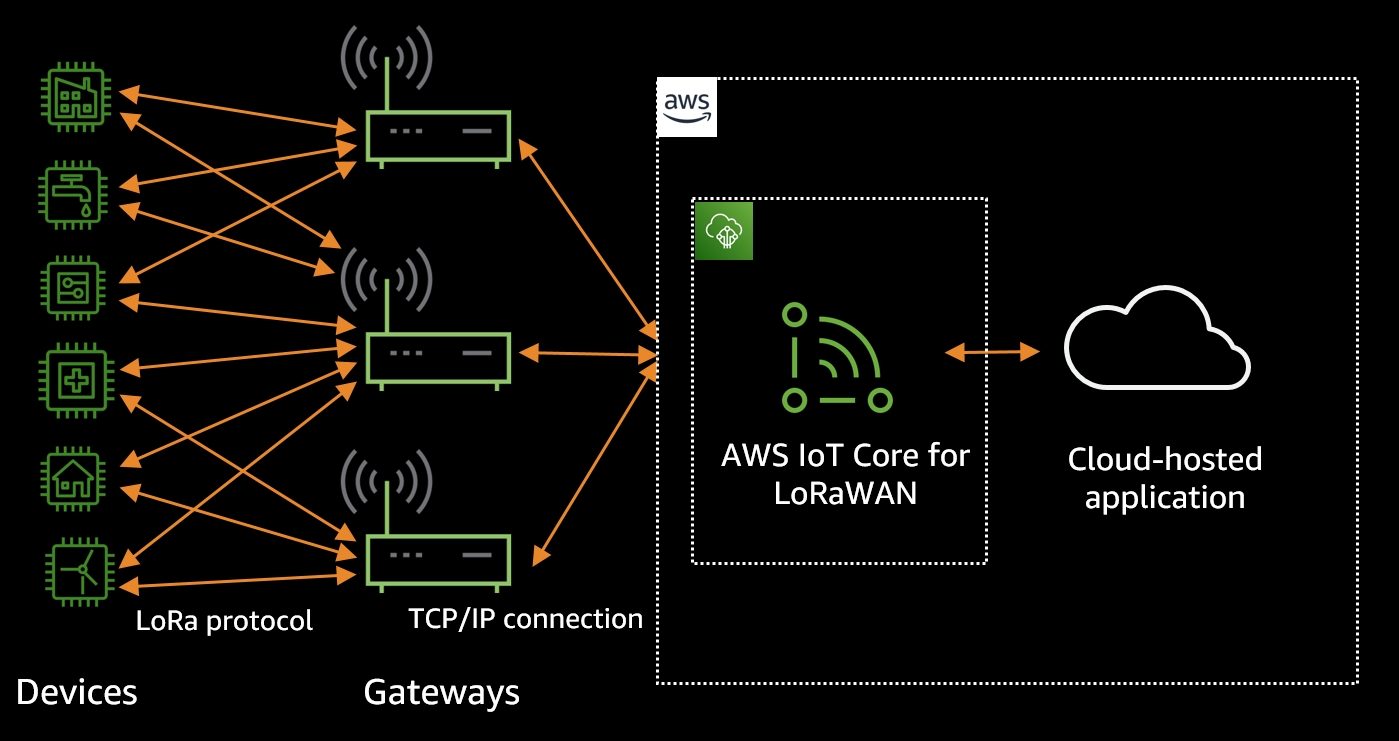
In today's rapidly evolving digital landscape, securely connecting remote IoT (Internet of Things) Virtual Private Clouds (VPCs) has become a crucial aspect of network management. As businesses and individuals increasingly rely on IoT devices, ensuring the secure transmission of data between these devices and the cloud is paramount. By effectively securing these connections, organizations can safeguard sensitive information, prevent unauthorized access, and maintain the integrity of their IoT ecosystems.
Achieving a secure connection for remote IoT VPCs involves a combination of robust network architecture, advanced security protocols, and continuous monitoring. These elements work in tandem to create a secure environment where IoT devices can communicate with the cloud without compromising data security. As the number of connected devices continues to grow, adopting best practices for securely connecting IoT VPCs is essential for mitigating risks and ensuring seamless operations.
In this comprehensive article, we will explore various strategies and techniques for securely connecting remote IoT VPCs. From understanding the fundamental concepts of IoT and VPC technology to implementing cutting-edge security measures, we will provide insights into creating a secure and efficient network. Whether you're a seasoned network administrator or new to the world of IoT, this guide will equip you with the knowledge and tools needed to protect your IoT infrastructure.
Table of Contents
- Understanding IoT and VPC
- Importance of Securing IoT VPC Connections
- How Does IoT Technology Work?
- What is a Virtual Private Cloud?
- Key Security Challenges in IoT VPC
- Best Practices for Securing Remote IoT VPC
- Secure Network Architecture for IoT
- How to Implement Advanced Security Protocols?
- What Role Does Encryption Play in Security?
- Continuous Monitoring and Threat Detection
- Securely Connect Remote IoT VPC
- How to Test the Security of Your IoT VPC?
- Case Studies of Successful IoT VPC Security
- FAQs
- Conclusion
Understanding IoT and VPC
The Internet of Things (IoT) refers to a network of physical devices that are connected to the internet, allowing them to collect and exchange data. These devices, ranging from smart home appliances to industrial sensors, interact with each other to perform various functions. The Virtual Private Cloud (VPC), on the other hand, is a secure and isolated cloud computing environment that provides scalable resources and a high degree of control over network settings. Together, IoT and VPC form a powerful combination, enabling efficient data management and processing in a secure manner.
Importance of Securing IoT VPC Connections
Securing IoT VPC connections is vital for protecting sensitive data and maintaining the reliability of IoT networks. Unsecured connections can lead to data breaches, unauthorized access, and potential manipulation of IoT devices. By implementing robust security measures, organizations can ensure that their IoT infrastructure remains resilient against cyber threats, safeguarding both operational efficiency and customer trust.
How Does IoT Technology Work?
IoT technology functions through a combination of sensors, connectivity, data processing, and user interfaces. Sensors collect data from the environment, which is then transmitted via internet protocols to a cloud server where it is processed and analyzed. Users can access this information through an interface, enabling them to monitor and control IoT devices remotely. This seamless flow of data is what makes IoT technology so powerful and versatile.
What is a Virtual Private Cloud?
A Virtual Private Cloud (VPC) is a customizable and isolated cloud environment provided by cloud service providers. It offers users a private segment within a public cloud, allowing them to configure network settings, define access controls, and manage resources independently. VPCs are designed to provide the benefits of cloud computing—such as scalability and cost-efficiency—while maintaining a high level of security and privacy.
Key Security Challenges in IoT VPC
Securing IoT VPCs presents several challenges, including:
- Device Authentication: Ensuring that only authorized devices can access the network.
- Data Encryption: Protecting data in transit and at rest from unauthorized access.
- Network Segmentation: Isolating different parts of the network to limit the impact of potential breaches.
- Vulnerability Management: Identifying and addressing security flaws in IoT devices and network infrastructure.
- Compliance: Adhering to industry regulations and standards to protect data privacy and security.
Best Practices for Securing Remote IoT VPC
Implementing best practices is crucial for ensuring the security of remote IoT VPCs. These practices include:
- Regularly updating IoT devices and network infrastructure with the latest security patches.
- Implementing strong access controls and multi-factor authentication for network access.
- Using encryption protocols like TLS and SSL to protect data in transit.
- Establishing network segmentation to isolate different components of the IoT network.
- Conducting regular security audits and vulnerability assessments.
Secure Network Architecture for IoT
Designing a secure network architecture is fundamental to protecting IoT VPCs. This involves creating a layered security model that includes:
- Perimeter Security: Using firewalls and intrusion detection systems to monitor and control incoming and outgoing traffic.
- Application Security: Implementing security measures within IoT applications to prevent unauthorized access and data breaches.
- Data Security: Encrypting sensitive data both in transit and at rest to prevent unauthorized access or tampering.
- Endpoint Security: Securing individual IoT devices with antivirus software and ensuring they are regularly updated.
- Monitoring and Analytics: Continuously monitoring network traffic to identify and respond to potential threats in real-time.
How to Implement Advanced Security Protocols?
Advanced security protocols are essential for protecting IoT VPCs from sophisticated cyber threats. To implement these protocols effectively:
- Adopt end-to-end encryption to secure communication between IoT devices and the cloud.
- Utilize secure tunneling protocols such as VPNs to protect data transmission over public networks.
- Deploy advanced authentication mechanisms like biometrics or token-based authentication for added security.
- Incorporate intrusion detection and prevention systems to identify and mitigate potential threats.
- Implement role-based access controls to restrict access based on user roles and responsibilities.
What Role Does Encryption Play in Security?
Encryption is a critical component of IoT VPC security, as it protects data from unauthorized access and tampering. By converting data into an unreadable format, encryption ensures that even if data is intercepted, it cannot be understood by unauthorized parties. Implementing strong encryption protocols such as AES (Advanced Encryption Standard) or RSA (Rivest-Shamir-Adleman) can significantly enhance the security of IoT VPCs.
Continuous Monitoring and Threat Detection
Continuous monitoring and threat detection are vital for maintaining the security of IoT VPCs. By employing advanced monitoring tools and techniques, organizations can identify potential threats in real-time and respond promptly. This proactive approach helps prevent security breaches and ensures that any vulnerabilities are addressed before they can be exploited.
Securely Connect Remote IoT VPC
To securely connect remote IoT VPCs, organizations must establish a secure connection framework that includes:
- Implementing VPNs or dedicated private connections to ensure secure data transmission.
- Using network access control lists (ACLs) to define and enforce security policies.
- Conducting regular security assessments to identify and mitigate potential vulnerabilities.
- Collaborating with cloud service providers to utilize built-in security features and services.
How to Test the Security of Your IoT VPC?
Testing the security of your IoT VPC is essential for identifying potential weaknesses and ensuring robust protection. Effective methods for testing IoT VPC security include:
- Conducting penetration testing to simulate attacks and identify vulnerabilities.
- Performing security audits to assess compliance with industry standards and regulations.
- Using automated vulnerability scanners to detect and address security flaws.
- Engaging third-party security experts to conduct independent assessments and provide recommendations.
Case Studies of Successful IoT VPC Security
Examining case studies of successful IoT VPC security implementations can provide valuable insights into effective strategies and practices. These case studies highlight how organizations have successfully addressed security challenges and protected their IoT infrastructure from cyber threats. By learning from these examples, businesses can enhance their own security measures and improve their overall cybersecurity posture.
FAQs
What is the importance of IoT VPC security?
IoT VPC security is crucial for protecting sensitive data, preventing unauthorized access, and ensuring the reliable operation of IoT devices.
How can I ensure secure data transmission in IoT VPCs?
Secure data transmission can be achieved by implementing encryption protocols, using VPNs, and employing secure tunneling techniques.
What are some common security protocols for IoT VPCs?
Common security protocols for IoT VPCs include TLS (Transport Layer Security), SSL (Secure Sockets Layer), and VPNs (Virtual Private Networks).
Why is network segmentation important for IoT security?
Network segmentation is important for isolating different parts of the network, limiting the impact of potential breaches, and enhancing overall security.
How often should I conduct security audits for my IoT VPC?
Security audits should be conducted regularly, ideally quarterly, to ensure ongoing compliance and address any emerging vulnerabilities.
What role do cloud service providers play in IoT VPC security?
Cloud service providers offer built-in security features and services that can be leveraged to enhance the security of IoT VPCs.
Conclusion
In conclusion, securely connecting remote IoT VPCs is essential for protecting sensitive data, ensuring reliable network operations, and safeguarding against cyber threats. By understanding the intricacies of IoT and VPC technology, implementing advanced security protocols, and adopting best practices, organizations can create a robust security framework that meets the demands of the modern digital landscape. Continuous monitoring, testing, and collaboration with cloud service providers further enhance the security posture of IoT VPCs, enabling businesses to thrive in an increasingly connected world.